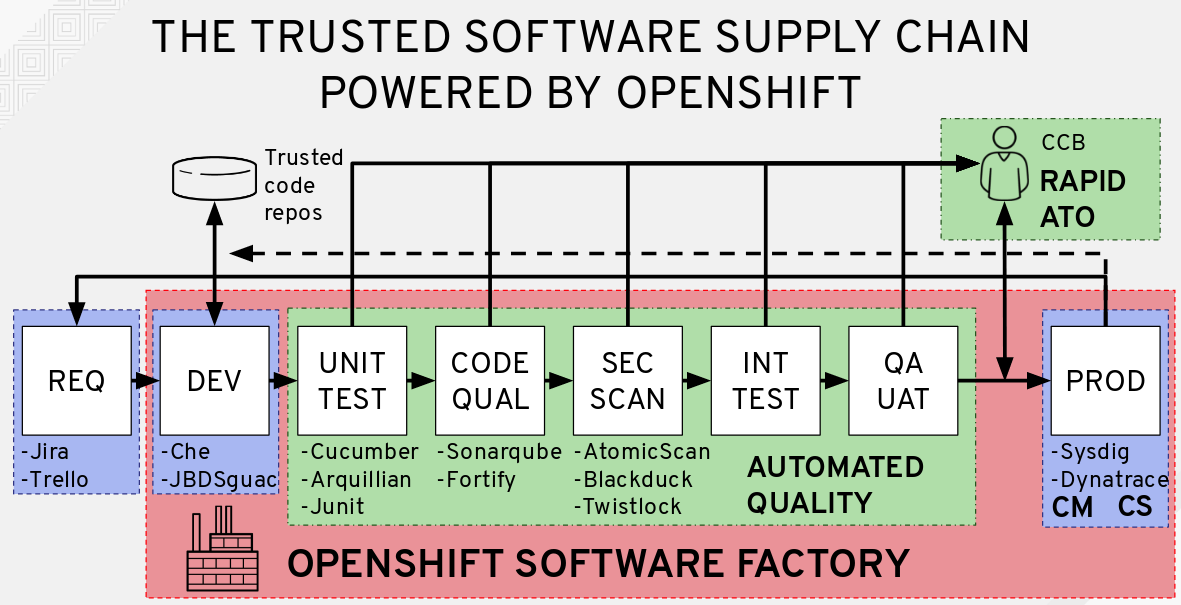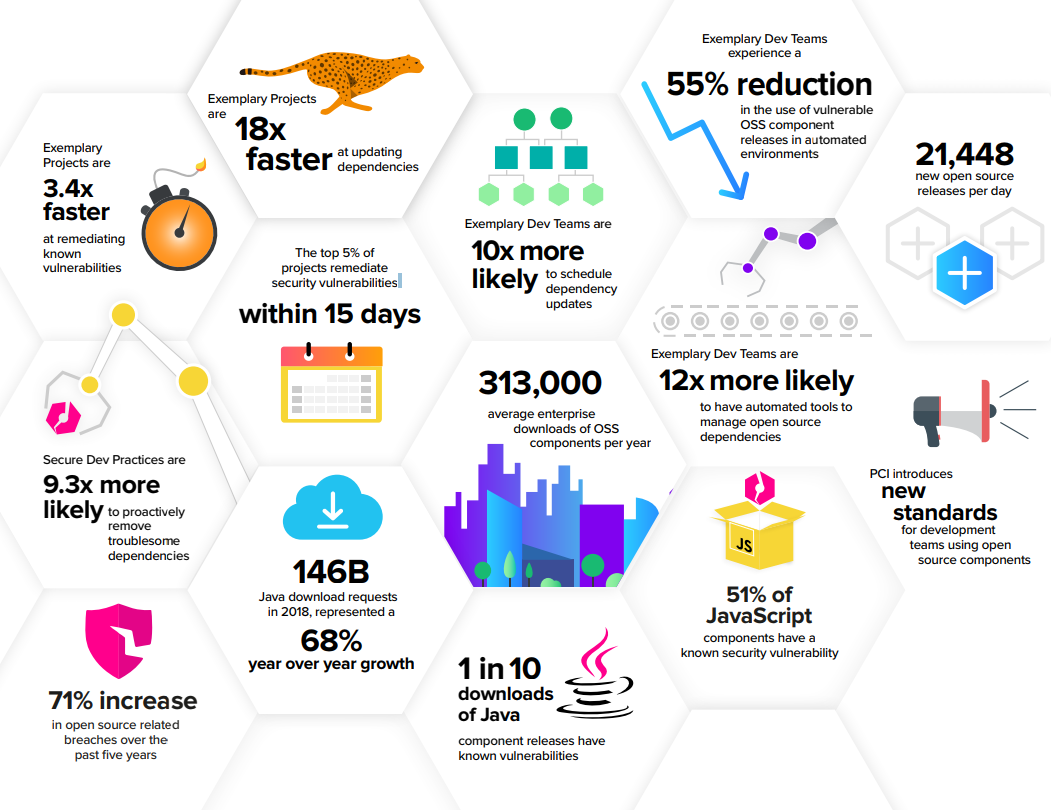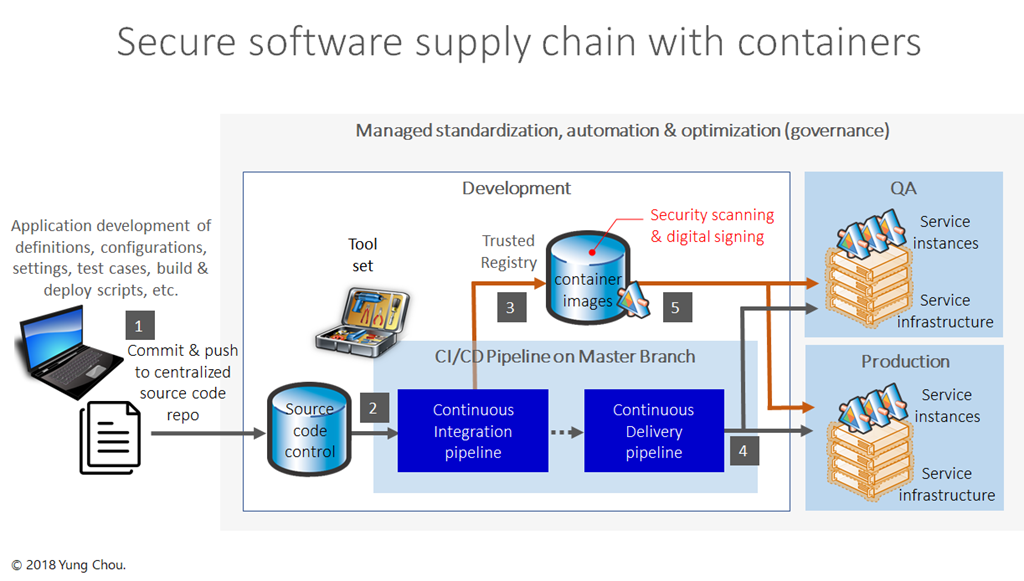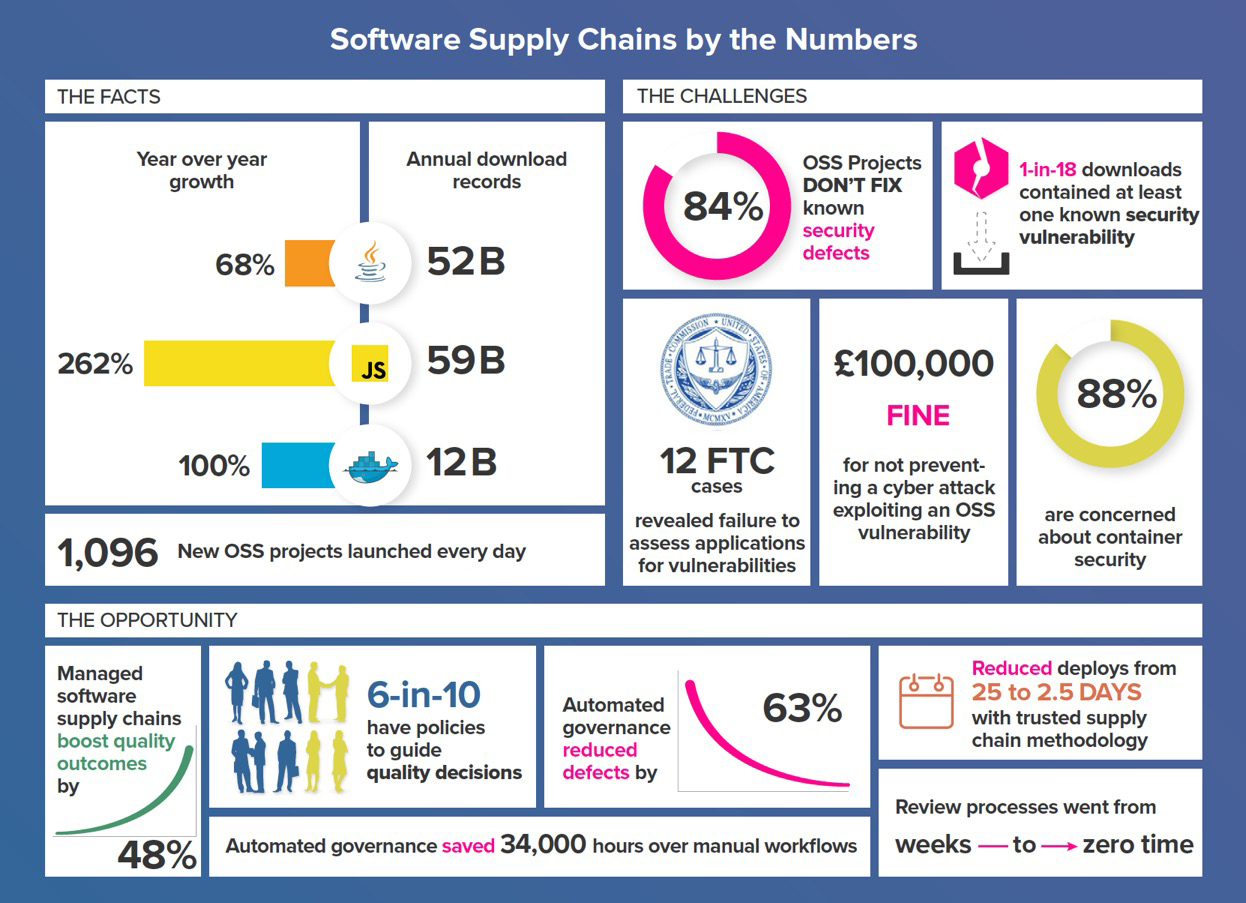
Sonatype 2017 State of the Software Supply Chain Report Reveals DevOps Practices Reduce Use of Defective Open Source Components by 63 Percent | Business Wire
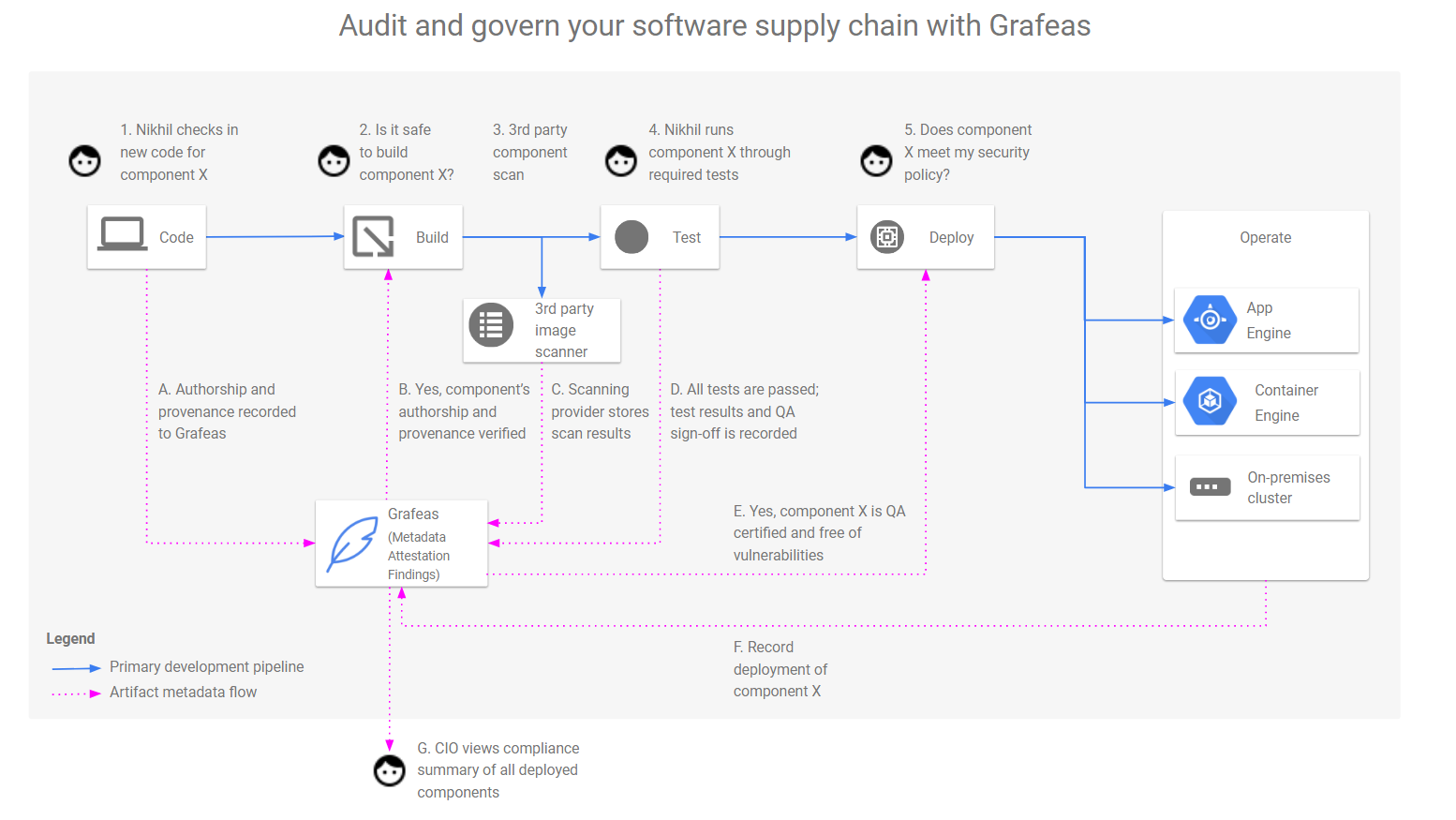
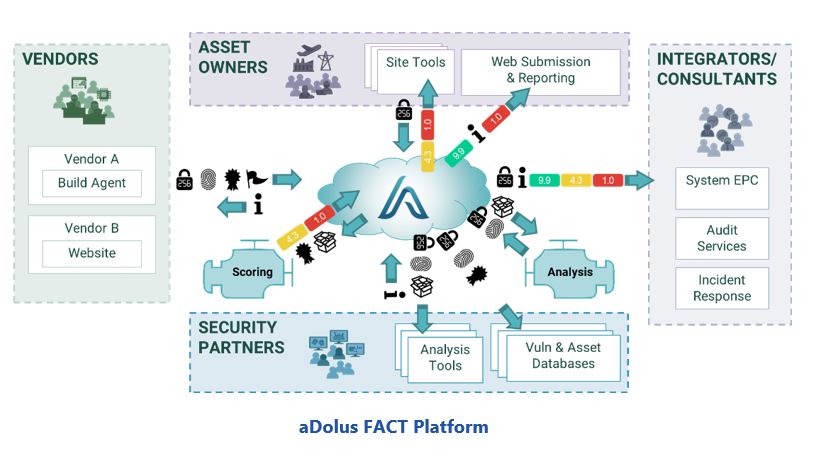
Google, IBM and others launch an open-source API for keeping tabs on software supply chains | TechCrunch